Brand Protection with Secure NFC Tags
Enterprise feature in betaThis feature is available only to our Enterprise customers and is currently in beta. If you're interested in using this feature, contact us.
Cryptographically secure NFC tags are a new generation of NFC tags that are very difficult to counterfeit but still work with existing NFC readers, such as most modern smartphones.
In this tutorial, you'll learn how to use and manage cryptographically secure NFC tags with the EVRYTHNG Product Cloud. What makes these tags special is that they generate a unique signature for every scan. Cryptographically secure tags, provisioned for the EVRYTHNG Product Cloud, contain the unique signature in query string parameters of a GS1 Digital Link. The EVRYTHNG Secure NFC Gateway allows brand owners to write redirection rules based on the result of decrypting the signature of tags. This allows you to redirect to different experiences, depending on the results.
How the URL of a Secure NFC Tag Protects Against Counterfeits
We currently support two secure NFC tag providers, NXP and EM Microelectronic. Both tags, NXP's NTAG 424 DNA and EM Microelectronic's em|echo-V tags, contain a secret AES-128 symmetric key that's stored in secured memory space. Each time a tag is scanned, the tag increases its counter by one, and then generates a cryptographically secure signature by encrypting the UID (or EPC) and counter together. It then adds the signature to its Digital Link and returns the entire URL to the reader.
NFC tag providers use slightly different approaches in the way they manage tag security and format URLs, which is why the EVRYTHNG Secure NFC Gateway uses a plugin architecture to accommodate these differences. Without going into details, consider the different URL templates. Both tags use the GS1 Digital Link standard, but the query string parameters differ:
For the NTAG 424 DNA, the enc parameter contains the UID and counter encrypted.
For example, the first scan returns:
https://nxp.snfc.evrythng.io/01/860080001331/21/347834?enc=837F4D3334D9FE435B7463C15F47E744&c=91776006C3328653Scan again and notice how enc has changed:
https://nxp.snfc.evrythng.io/01/860080001331/21/347834?enc=712552534214C3A0B70B2054B23889FA&c=7800BD167C1F84A0For the em|echo-V tag, the signature is contained in the aes parameter. It's the encrypted combination of the EPC and counter.
For example, the first scan returns:
https://em.snfc.evrythng.io/01/860080001362/21/8b17eccfbd71a453?epc=4oCxECAA-AESAn16&token=AAA3&f=A&aes=TcD5LBeh4uQSnruMff6EJQScan again and notice how aes changed:
https://em.snfc.evrythng.io/01/860080001362/21/8b17eccfbd71a453?epc=4oCxECAA-AESAn16&token=AAA5&f=A&aes=l2MMKs5JwczhGXbm7E28XgArchitecture
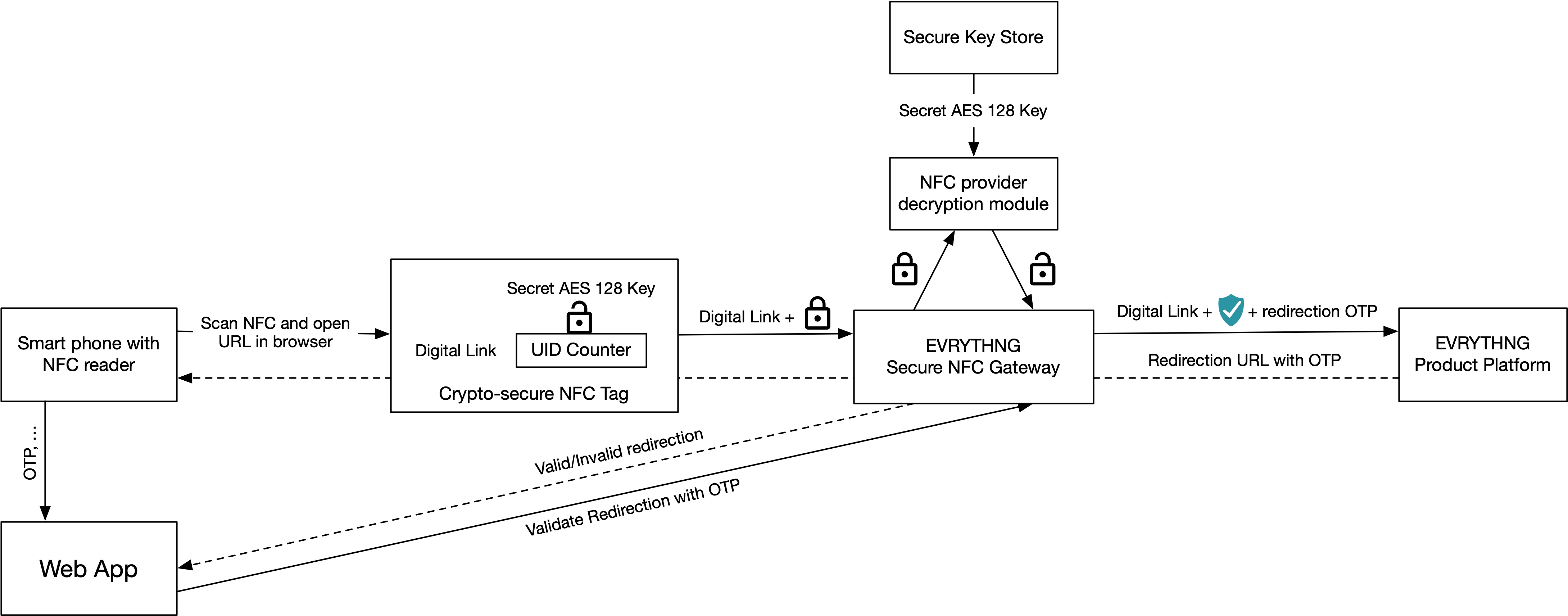
EVRYTHNG Secure NFC Gateway Architecture
The EVRYTHNG Secure NFC Gateway adds support for cryptographically secure NFC tags to the EVRYTHNG Redirector. The architecture shows an NFC tag with a secret AES-128 key, a tag-specific UID (or EPC), a counter and a Digital Link. The Digital Link maps to a Thng, the other components secure the tag. As mentioned, the tag generates a new URL every time it's scanned.
Unlike redirections triggered by scanning a QR code or regular NFC tag, the URL of a cryptographically secure NFC tag goes through the EVRYTHNG Secure NFC Tags Gateway, before reaching the EVRYTHNG Redirector. The gateway uses provider-specific modules to decrypt and authenticate each request. AES-128 is a symmetric protocol, so the tag and gateway use the same key to encrypt and decrypt. The gateway also keeps track of the scan counter by storing it as a Thng Property. Comparing the decrypted counter and the Thng's counter shows URLs being used more than once.
Note that a secure NFC tag can only prevent a tag from being copied. A counterfeiter could still store the redirection URL on an NFC tag. To prevent a redirection from being reused, the gateway generates a new one-time password for every redirection, which the gateway encrypts with its private key. The web client gets the corresponding public key from the domains EVRYTHNG app. If the one-time password expires, the client knows the redirection is invalid.
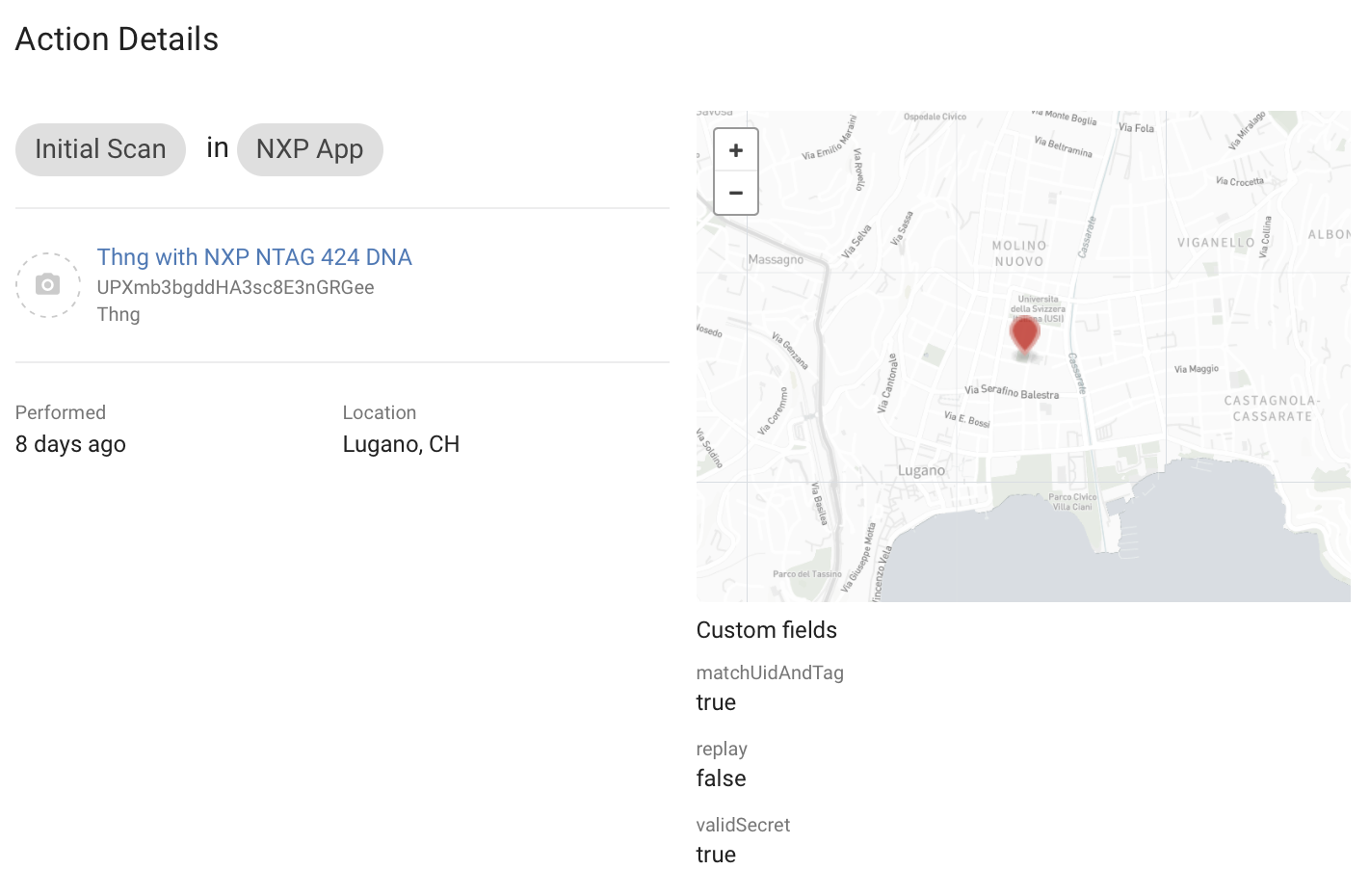
Implicit Scan action for an authentic tag
The gateway creates an Implicit Scan Action with the authentication result from the provider-specific module as custom fields. These values can be used in a redirection rule header and body. The action above shows the tag is authentic.
Use Case: Barry the Bear Endorses the EVRYTHNG Secure NFC Gateway

Spot the secure Barry
We asked Barry the Bear, the famous GS1 Digital Link mascot, to try the EM Microelectronic em|echo-V tag. The em|echo-V tag is a dual frequency tag that supports NFC and RFID.
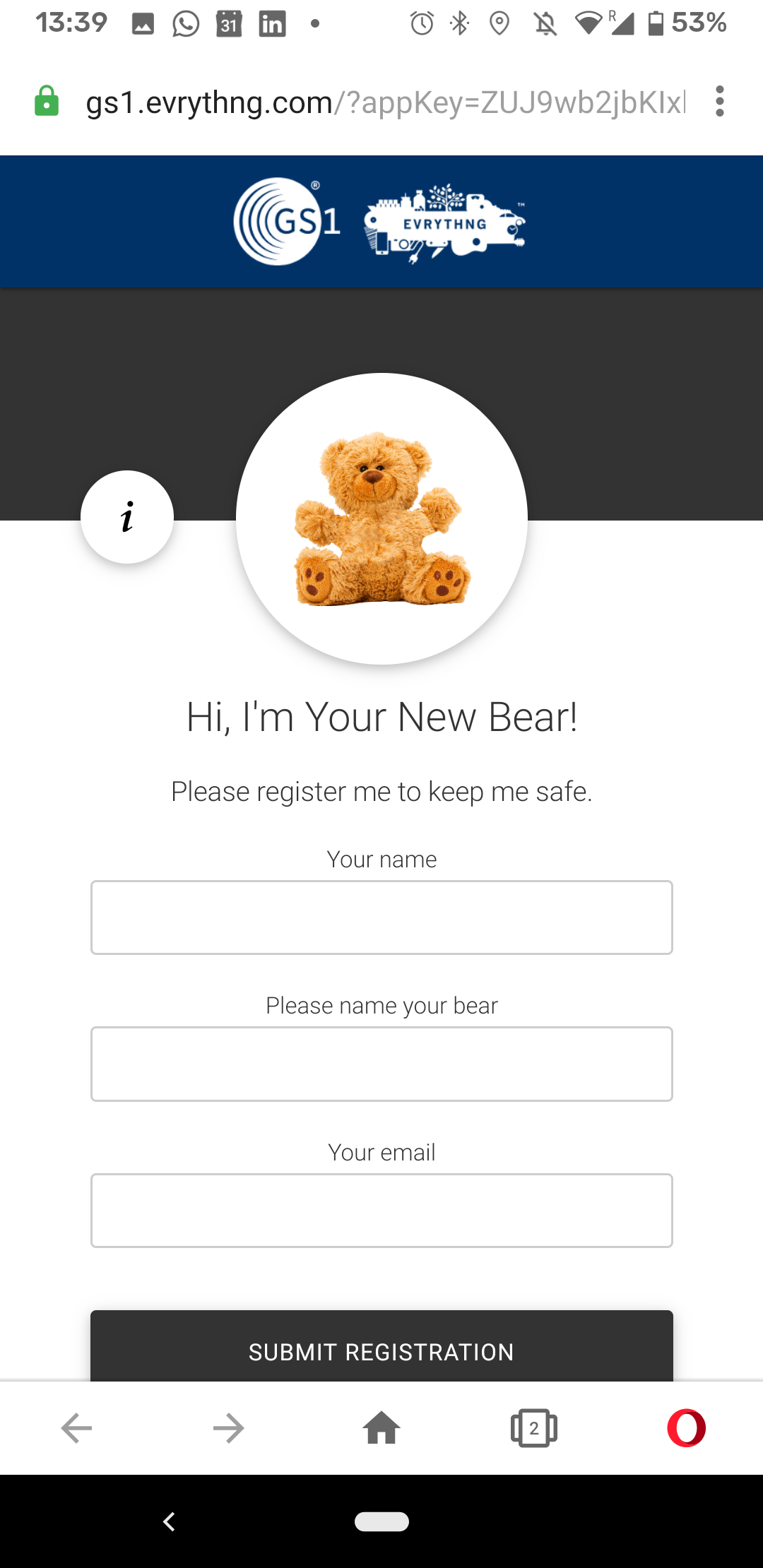
Barry the Bear web experience
To test the EVRYTHNG Secure NFC Gateway, hold your smart phone close to the label of Barry the Bear. Your phone reads the NFC tag and open the Digital Link in the browser. If the tag is authentic, you are redirected to the default Barry the Bear web experience.
What happens if a Barry the Bear impostor tries to copy and reuse a signed URL? After all, the signature is authentic and the EVRYTHNG Secure NFC Gateway can authenticate the signature.
Scan this QR code to find out.

Simulate a replay attack
Three redirection rules map the authentication outcome to different URLs.
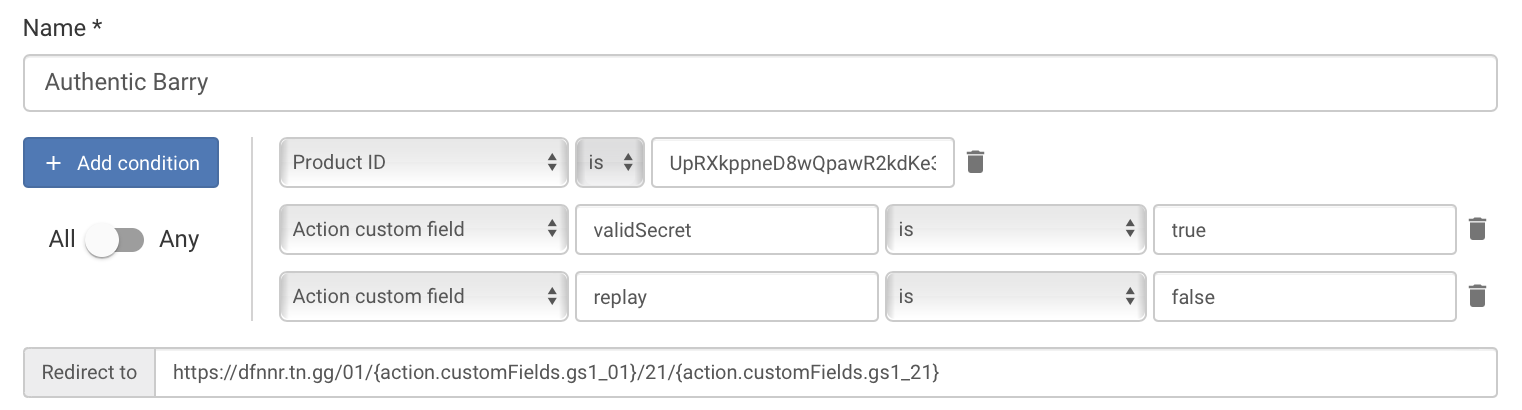
Redirection for authentic tags
If the tag is authentic, the user is redirected to the Barry to Bear web experience.
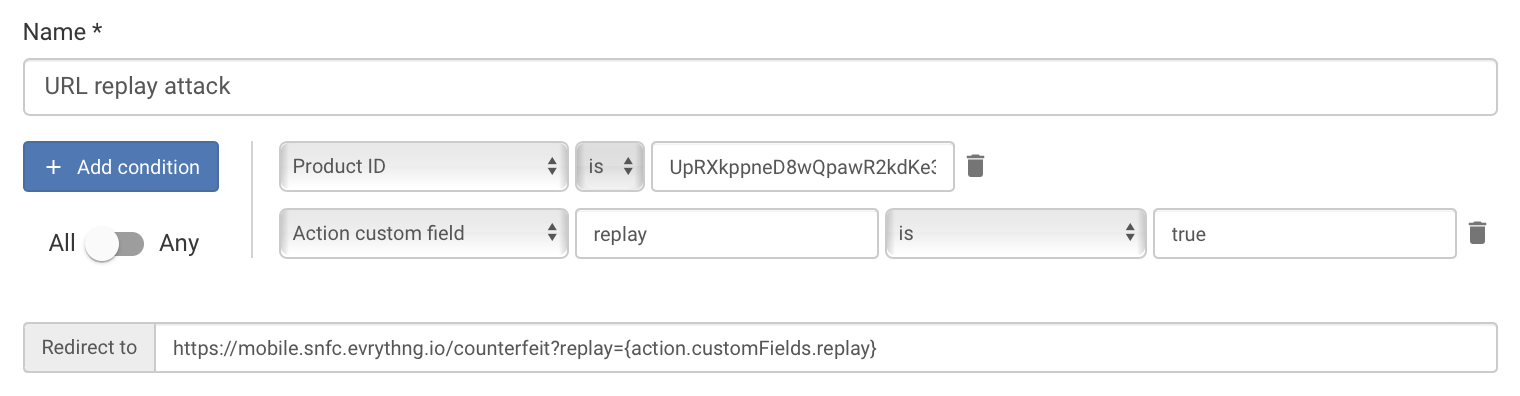
Redirection for counterfeit tags. The URL was used twice.
If the signature can be decrypted but the URL was used twice (the URL counter is lower or equal to the Thng's counter), the user is redirected to a site, showing the URL was replayed. This is how a Barry the Bear impostor is detected.
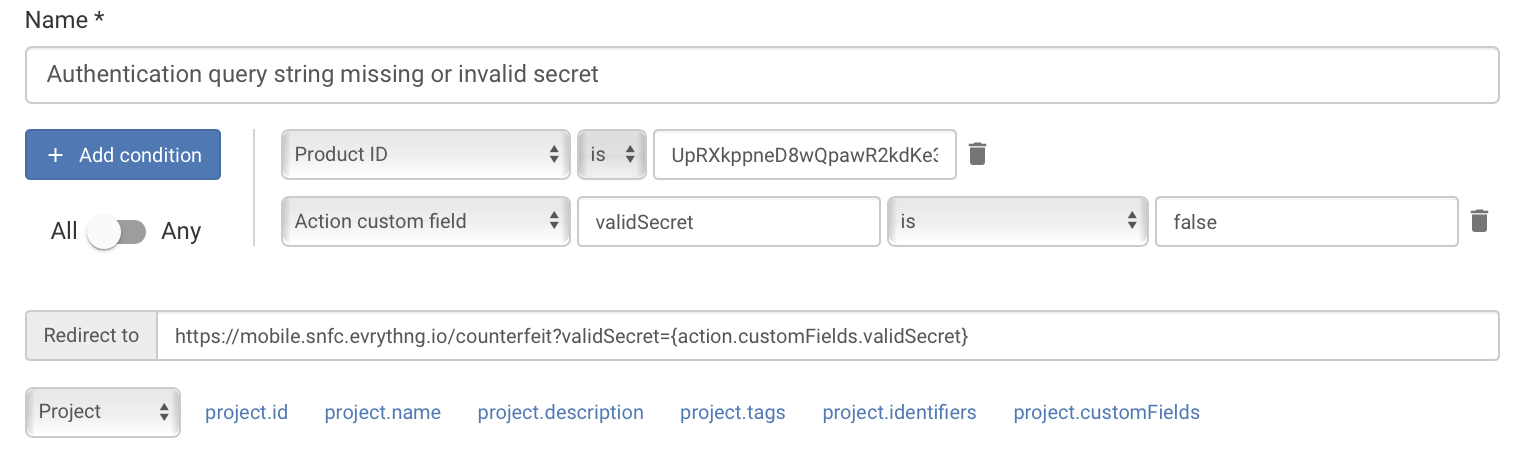
Redirection for counterfeit tags that could not be authenticated
If the signature can't be decrypted because the signature is wrong or entirely missing, the user is redirected to a site warning them of that fact.
Adding New Tags to the EVRYTHNG Product Cloud
You might have asked yourself how the EVRYTHNG Secure NFC Gateway knows which provider and security credentials to use and how to access Thngs. It does this through the domain name used in the tag's URL. A cryptographically secure tag belongs to one redirection domain. A redirection domain comprises a domain name, a Trusted App API key, a provider and security credentials required by the provider and a set of tags of the same type.
Let's go step by step through adding a new set of secure NFC tags.
Create a Project and EVRYTHNG Application
This EVRYTHNG Application provides access for the EVRYTHNG Secure NFC Gateway to Thngs. It must contain at least one redirection rule related to tag authentication.
Get a Domain Name and Create Valid GS1 Digital Links for Thngs
Your tags must contain valid Digital Link URLs. Because all requests must go through the EVRYTHNG Secure NFC Gateway, you must configure a domain name to point to snfc.evrythng.io, the EVRYTHNG Secure NFC Gateway's host name. Optionally, the parameter validFor can be specified to set the timeout for the one-time password that can secure the redirection URL.
When a domain is registered, the EVRYTHNG Secure NFC Gateway generates a private/public key pair to secure the redirection. The EVRYTHNG Secure NFC Gateway stores the public key as a custom field for its EVRYTHNG application. A user-experience can secure the redirection by including a one-time password. The gateway generates a one-time password for every request. It can be added to the redirection as query string parameter: otp={action.customFields.otp} .
Besides the query string parameter otp, the web client requires an EVRYTHNG App API key and the ID of the Thng, which maps to the secure NFC tag. The web client decrypts the one-time password and raises an alert if the redirection is expired. To flag expired one-time passwords, we recommend creating an alert in the dashboard by creating an _InvalidClientRedirections action. The gateway provides a redirection validation endpoint that performs all the previous steps.
GET https://nxp.snfc.evrythng.io/thngs/UQhhVxe7fFCXDdgtQ3aGtkEs/validateRedirection?otp=99cc18...223b&apiKey=uKKz...1TLKmNote that the App API key is also a query parameter to avoid Cross-Origin Resource Sharing (CORS) errors. If the redirection is valid, the gateway returns HTTP status code 200. If the redirection expired, the HTTP status code is 498.
To test the redirection validation feature in your web client, use this code:
const url = new URLSearchParams(window.location.search);
if (url.get('otp') === null)
throw new Error("No one-time password found (query string parameter 'otp' is missing) Add the one-time password in the Redirector as follows: otp={action.customFields.otp}");
const otp = url.get('otp');
const apiKey = url.get('apiKey') || url.get('app');
if (apiKey === null)
throw new Error('EVRYTHNG App API key is missing');
const thngId = url.get('thng');
if (thngId === null)
throw new Error('thng Id is missing');
const request = new Request(`https://nxp.snfc.evrythng.io/thngs/${thngId}/validateRedirection?otp=${otp}&apiKey=${apiKey}`);
const response = await fetch(request);
if (+response.status !== 200) {
if (+response.status === 498) {
alert('Invalid redirection');
} else {
alert('Something went wrong');
}
}Create a Redirection Domain
When registering a redirection domain, the EVRYTHNG Secure NFC Gateway generates a unique AES-128 key (returned in secretKey) to encrypt and decrypt security-relevant information. It also creates a private and public key-pair to authenticate redirections.
POST https://snfc.evrythng.io/domains
Authorization:EU9Sw...KeOvD
{
"domain":"yourdmain.example.com",
"validFor": 5,
}{
"domain":"yourdmain.example.com",
"secretKey": "652c8...95a76",
"otpPublicKey": "-----BEGIN PUBLIC KEY-----\nMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvPCcIrPxdFppmqjWk1fk\nswoc8zBhZmi31Ikym+ECsTBkuXDtKZ98C4+LOi27MvleJ9RYrvt2hML1lKmAript\nsLr+YN2ISAi8jWblPywL+fgEQyPhJZUzdMiSxsDj8jg5cG0+ZpjOz4YHeCL2PJ2R\nfgpMV4CfBjvGPEGfGeweOT/Zky+VRA9OSXWhEDUdsIW4jru4DY/G/4dvwUwNJoqa\nrx7yPwTyvHe15t2lSk/8rtdVfGo39ipArUCcGiWM4UumZoyIGfSyxtFdPVv7z6td\nhC5AnOtXD0/Em8gH5y7Q52jFR+ddeMJRBqa+51HU9+tXvGH68b39qFqlNZjvcoVJ\ntQIDAQAB\n-----END PUBLIC KEY-----\n",
"trustedAppApiKey": "EU9Sw...KeOvD"
}Set Up Tag Credentials
Configure the authentication mechanism by specifying the provider and provider-specific security information.
Configuring a Domain for NXP NTAG 424 DNA
NXP NTAG 424 DNA tags can be verified using NXP's remote service, Authenticator v2 API, or by verifying the URL locally using the private key. To use NXP Authenticator v2 API, the configuration requires provider==nxp, keyIdMetaRead, keyIdFileAccess, nTagApiKey and provider:
POST https://snfc.evrythng.io/yourdmain.example.com/credentials
Authorization:EU9Sw...KeOvD
{
"keyIdFileAccess": "13",
"keyIdMetaRead": "12",
"nTagApiKey": "64b8cb...949efe",
"provider": "nxp"
}To verify NXP NTAG 424 DNA tags locally, use provider==nxp-local and the parameter symmetricTagKey which contains the same symmetric key that is stored on the tags
POST https://snfc.evrythng.io/yourdmain.example.com/credentials
Authorization:EU9Sw...KeOvD
{
"provider": "nxp-local",
"symmetricTagKey": "FFAE0...01C6"
}Configuring a Domain for em | echo-V Tags
EM Microelectronic requires only the otp, the AES-128 OTP Crypto Key:
POST https://snfc.evrythng.io/yourdmain.example.com/credentials
Authorization:EU9Sw...KeOvD
{
"otp": "F0..00",
"provider": "em"
}Add Redirection Rules to the Redirector
You'll need redirection rules that respond to the state of a tag as shown in the beginning of the tutorial. The EVRYTHNG Secure NFC Gateway sends the following Action custom fields to the Redirector (for example, action.customFields.replay):
-
validSecret:trueif the signature was successfully verified, orfalseif the signature is missing or could not be decrypted. -
replay:truemeans the signature was successfully verified, but the URL was already used. It's a counterfeit tag, even thoughvalidSecretis true. -
matchUidAndTag:truemeans the signature doesn't match the tag. The signature is valid, but it belongs to a different tag. -
validTagis a summary feature of the verification process.validTagis true ifvalidSecretistrue,replayisfalseandmatchUidAndTagis alsotrue.
Each Thng must be assigned to a Product and both need a valid GS1 identifier. The Product needs the identifier gs1:01, and the Thng needs the identifier gs1:21.
Updated 9 months ago
